Difference between revisions of "Nick Apseloff"
(→Goal 8 (Javanotes Ch 2.1-2.2)) |
(→Goal 8 (Javanotes Ch 2.1-2.2)) |
||
| Line 242: | Line 242: | ||
====Goal 8 (Javanotes Ch 2.1-2.2)==== | ====Goal 8 (Javanotes Ch 2.1-2.2)==== | ||
1. Briefly explain what is meant by the syntax and the semantics of a programming language. Give an example to illustrate the difference between a syntax error and a semantics error. | 1. Briefly explain what is meant by the syntax and the semantics of a programming language. Give an example to illustrate the difference between a syntax error and a semantics error. | ||
| − | :*The syntax of a language consists of the rules and vocabulary that allow the program to be compiled and executed. Programs that contain syntax errors are rejected and fail to compile. | + | :*The syntax of a language consists of the rules and vocabulary that allow the program to be compiled and executed. Programs that contain syntax errors are rejected and fail to compile. The semantics of a program is its meaning. A program with correct semantics does what you wanted it to do. An example is if your syntax was correct, that is your code was written properly with no mistakes, but the result is "!dlroW olleH" instead of "Hello World!". There is no error in compiling because all of the syntax is correct, but the semantics are wrong because the program did not do what it was meant to do. |
| + | |||
| + | 2. What does the computer do when it executes a variable declaration statement. Give an example. | ||
==See also== | ==See also== | ||
Revision as of 22:39, 16 January 2009
My name is Nick Apseloff, (pronounced /ˈæpsəlˌɒff/) and this is my wiki for Mr. Bui's advanced topics class.
Contents
- 1 1st Quarter
- 1.1 Goals
- 1.2 Documentation
- 1.2.1 Goal 1 (The network)
- 1.2.2 Goal 2 (Packet sniffers)
- 1.2.3 Goal 3 (Instant messenger messages)
- 1.2.4 Goal 4 (Instant messenger password)
- 1.2.5 Goal 5 (Gmail log-in)
- 1.2.6 Goal 6 (Gmail chat)
- 1.2.7 Goal 7 (Gmail e-mail)
- 1.2.8 Goal 8 (SSL/TLS)
- 1.2.9 Goal 9 (Ethernet cable)
- 1.2.10 Goal 10 (Firewall)
- 2 2nd Quarter
- 3 See also
- 4 References
1st Quarter
Goals
1. Set up a small network of 3 computers using a hub. [X]
2. Research packet sniffers. [X]
3. Intercept instant messages sent from one computer to another on the network. [X]
4. Intercept instant messenger password information sent during log-in. [X]
5. Intercept log-in information sent when someone logs onto Gmail. [X]
6. Intercept Gmail chat messages using the packet sniffer. [X]
7. Intercept an e-mail sent through the hub from another computer on Gmail. [X]
8. Research SSL/TLS. [X]
9. Make an ethernet cable to connect the switch to the new firewall. [X]
10. Set up the firewall for the network. [X]
Documentation
Goal 1 (The network)
Willie Stehm, AJ McLennan, and I set up a network of three computers. We installed Xubuntu 8.04 (a Linux distribution) on each machine and then networked them together using ethernet cables (like the own shown at the top of the page) and a hub. We chose Xubuntu as our operating system because it is completely free to download and use and requires much less memory to operate (which was a necessity since all three computers are relatively old).
Goal 2 (Packet sniffers)
A packet sniffer is a device or program that allows eavesdropping on traffic traveling between networked computers.[1] Every time you view a webpage or communicate with someone over the Internet, your computer sends packets requesting something and you receive packets with what you requested. In the example of a webpage, you send a request to the server that holds the webpage information, the hypertext is sent to you, and your browser converts that hypertext into a viewable site. But when those packets are intercepted by another machine, they can analyze them and monitor your traffic. They can sometimes even see things such as passwords or other sensitive information sent. Packet sniffing has practical uses like observing Internet usage at schools or offices.
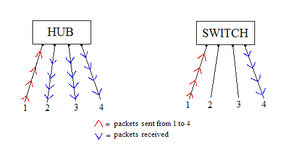
The reason that packet sniffing will work on our network is because we are using a hub, rather than a switch, to connect our computers. Hubs broadcast the packets sent by one computer to all ports, so viewing the packet activity of another computer is quite simple (see Figure A). On the other hand, switches send the packets to only the desired port, so others on the network cannot listen in on your traffic. Switches have replaced hubs almost entirely because of this blatant security flaw, but hubs are still used in some situations such as where security is not a necessity.
Goal 3 (Instant messenger messages)
We initially tried to get the program 'talk' working on the machines so we could easily send messages between two of the computers in an attempt to view the packets transmitted on the third computer. After a few days of trying to get it to work, with no success, we settled on using Pidgin (a messenger client that is compatible with AOL Instant Messenger).
We then downloaded a packet sniffer called 'Wireshark' and ran it on one of the computers. On AJ's computer, he signed onto AOL Instant Messenger using his own screen name. By changing the display filter of the packet sniffer to only show AIM packets, we were able to see his screen name when he logged on. It was difficult to decipher which packets corresponded to what he was doing, but after getting familiar with the descriptions of the packets it was easy to pick out the ones that were messages. We were able to read outgoing and incoming messages as well as buddy info that the other computer was viewing.
Goal 4 (Instant messenger password)
On Willie's computer, I typed in a random password to sign on just so I could see if we could view the password sent to AOL. We found the outgoing packet and not surprisingly, the password was not sent in plain text; it was sent as a password hash using the MD5 algorithm, short for Message-Digest algorithm 5. This algorithm uses a one way hash function (one way meaning that the function cannot be reversed) that translates the password to a 128-bit hash value (32 characters consisting of 0-9 and a-f). The purpose of the password hash is to prevent exactly what we were trying to do. We successfully sniffed the packet that contained the password sent, but all we got was the following irreversible password hash: 51e3ed91700bee528a11e333ab25e6d2. In Layman's terms, when you type in a password to sign into something, the password gets jumbled up into random letters and numbers before being sent, so anyone trying to steal your password by sniffing your packets will not be able to, or at least have a very difficult time doing so. It is theoretically possible to recover a plain text password from an MD5 password hash using a rainbow table, in which the hash value is compared to an extensive list of known hash values and their plain text form, but this is not a very feasible tactic. A seven character password has 6.98 x 10^13 possible combinations, and having a hash list of every single one of them would require hundreds of terabytes of storage.[2]
Goal 5 (Gmail log-in)
After our success with sniffing instant messenger packets and log-in information, we decided the next step would be to try to do the same with e-mail. When I loaded the Gmail log-in screen while sniffing packets on another computer, I noticed that Gmail uses a SHA hash function (Secure Hash Algorithm) in addition to RSA encryption when submitting your username and password to sign in.
RSA is recognized as one of the first encryption algorithms (1977) and is still used widely today. In the algorithm, there is a public key which is available to everyone and is used for encrypting messages, and there is a private key which is obviously kept private and is used for decrypting the messages encrypted by the public key. RSA is difficult to crack because the private key consists of two very large prime numbers, p and q, and they are multiplied together to get N. In order for someone to figure out the values of p and q, the private key, they would have to factor N, which would be extremely difficult considering the fact that p and q are both prime numbers possibly 100 to 200 digits long.[3]
The SHA hash function is similar to the MD5 hash function described in goal #2, but uses a 160-bit hash value instead of 128-bit. This means that the SHA hash is much harder to decrypt than MD5.[4]
Goal 6 (Gmail chat)
Since Gmail only uses encryption for logging into your account, we figured it would be possible to intercept and read Gmail chat activity. On Willie's computer we had Wireshark running and sniffing packets with a display filter only showing HTTP packets. We were unable to locate the packet that contained the message when AJ sent an e-mail from his computer, but it was surprisingly easy to intercept his Gmail chat conversation.
We started by looking at all of the packets that had the word 'mail' in the description header. The packets that had the word 'POST' in the description were Gmail chat packets, and we began to look through the detailed packet information. We found AJ's e-mail address, the e-mail address of the person AJ was chatting with, and even the text AJ was sending to that person. Another interesting thing we discovered was that every time AJ moved his mouse, a packet would be sent with the text "mouse_move" in the details. We deduced that this packet is what determined whether his computer was idle or not, and after a certain amount of time of him not typing and not moving his mouse, Gmail chat would automatically set his status as 'idle'.
In addition to seeing his chat activity, we were able to read messages from his inbox. Gmail refreshes the inbox after a certain period of time, and doing so resulted in an incoming packet that contained all of his inbox messages in plain text form. We were able to read the address of who the e-mail was from, as well as the subject and body of the e-mail.
I had previously assumed that the Gmail chat would be encrypted, but after further research I figured out more reasons why we were able to read AJ's messages. When communicating over Google Talk using the downloaded program, similar to AOL Instant Messenger, the connection is encrypted, but when using chat over HTTP in Gmail, there is no encryption.[5] This is a serious security flaw that obviously can be exploited with ease. I never would have known that there was no encryption had I not been experimenting with it. Essentially, sending information over a non-encrypted connection is like sending information to someone in a postcard; anyone who sees the postcard can read what is written on it because there is no form of security.
Goal 7 (Gmail e-mail)
It took a lot of tedious searching through packet contents to find it, but we were finally able to sniff an e-mail packet and read the text sent.
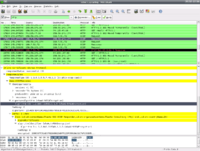
AJ sent an e-mail from his personal Gmail account to the account that we made (sniffmypackets@gmail.com) with the text "can you hear me now?". As you can see in the picture to the left, after digging through the packet details we found the data chunk that contained the body of the e-mail. Also, if you look up a few rows, you can see "test 3", which was the subject of the e-mail.
The reason that we were able to read the message without any trouble was the same as in the last goal. Gmail does not use any encryption for chat or e-mail; they only encrypt your log-in information.
Most Gmail users are completely unaware that the e-mails they send are completely unencrypted. This issue is surprisingly easy to fix, though. If you go into Gmail browser preferences, you can turn on SSL encryption by enabling 'https'.[6]
Goal 8 (SSL/TLS)
The SHA hash and RSA encryption algorithm from goal 5 are used in combination to form Gmail's SSL cipher.
SSL stands for Secure Sockets Layer, and it is a protocol designed by Netscape that accepts many different ciphers for secure communication over the Internet. This protocol, or set of rules, "allows an SSL-enabled server to authenticate itself to an SSL-enabled client, allows the client to authenticate itself to the server, and allows both machines to establish an encrypted connection."[7] It works mainly through public/private key encryption like the RSA concept.
TLS stands for Transport Layer Security, and it is the successor of SSL. Created by the Internet Engineering Task Force, TLS is very similar to it is more versatile with working on different ports and uses stronger encryption algorithms.[8]
The two are used in client-server transactions, like e-mail and instant messaging, and ensure that information is sent privately and has integrity. The algorithms used by both security protocols are very strong and difficult to break, which is why we would have a very hard time figuring out a password that we found in a Gmail log-in packet.
Goal 9 (Ethernet cable)
In order to complete our next goal (set up a firewall for our network), we had to have an ethernet cable around 15 feet long. The only cabling that we had to use was either nonfunctional or too short, so we had to make a cable of our own. We cut a length of cable off of a giant spool and gathered our tools together. We needed a splitter, a crimper, and two cable heads.
An ethernet cable consists of a plastic casing around 8 different colored wires. The splitter is used to cut about an inch of the plastic casing off of the end of the cable so that the wires are sticking out. The wires are in 4 pairs of 2, and the pairings are done by color (brown, blue, orange, and green; each pair has a solid and striped wire of each color). We then untwisted the pairs and straightened out each individual wire. For a category-5 ethernet cable, the order of colors in the cable head from left to right is green stripe, green, orange stripe, blue, blue stripe, orange, brown stripe, brown. We put them in this order, straightened them out, and cut the tips to make the end flat in order to insert them into the cable head. We slid the wires into the head of the cable, making sure they fell into the slots and the pins lined up and then crimped the head to permanently lock the wires into place so they don't fall out. The end product looked like the picture of the ethernet cable at the top of the page.
Goal 10 (Firewall)
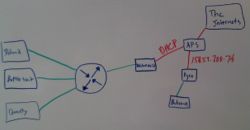
We started this goal by drawing a layout of our network and Mr. Bui's lab (shown to the right). The room consists of two firewalls connected to the Arlington Public Schools wide area network. Mr. Bui's firewall is connected to the lab and our firewall is connected to our mini-network. The circular symbol with the arrows is a hub.
We set up the firewall to use dynamic host configuration protocol (DHCP) for our network, which means that the computers would be automatically assigned an IP address. The firewall is a computer with two network interface cards, one of which is the 'red' interface and the other is the 'green' interface. The red interface card is connected to the Arlington Public Schools network and the green interface card is connected to our hub that branches out into our mini-network.
We installed IPCop, a Linux firewall distribution, on the machine that we designated as our firewall. After a lot of tweaking and trial and error, it was set up and working. The reason that we set it up was to be able to perform other network security projects in the future involving the firewall.
2nd Quarter
Goals
1. Research Wiimote. [X]
2. Research Wiimote head tracking. [X]
3. Build the infrared head tracking unit. [X]
4. Use the Wiimote as a mouse for the computer. [X]
5. Set up head tracking system. [X]
6. Read chapter 1 of Javanotes and take quiz. [X]
7. Install Java on home computer. [X]
8. Read chapter 2.1-2.2 of Javanotes and answer quiz questions 1-4. [ ]
9. [ ]
10. [ ]
Documentation
Goal 1 (Wiimote research)
The Wii works by using two infrared LEDs (light emitting diodes) on a sensor bar that are picked up by the infrared detector in the Wiimote controller. The controller tracks the movement of the LEDs and this information is sent to the Wii console via bluetooth, which makes games capable of being interactive because of real time tracking of the location of the remote. The Wiimote also contains an accelerometer, which measures the physical movement of the remote. For example, if you tilt the remote to the side, the accelerometer detects the magnitude and direction of the tilting, and sends this information to the Wii wirelessly using bluetooth. The Wii Sports bundle that comes with the system uses the accelerometer for every game. In tennis, for example, the user swings the Wiimote to hit the ball on the screen, and the accelerometer determines how hard the swing is and whether or not the timing was accurate. In addition to the innovative methods of input, the Wiimote has a vibrate function and a speaker.
The bluetooth connectivity works up to 30 feet away, but the maximum distance that the IR sensor can detect the sensor bar is up to 16 feet.
Goal 2 (Head tracking research)
Using a mounted Wiimote above the computer monitor and a head-mounted tracking unit with two infrared LEDs (essentially a sensor bar), it is possible to track the movement of a person's head, and use that information to change an image on the screen being viewed in order to significantly enhance the feel of virtual reality. We found a website made by Johnny Chung Lee, a researcher with a PhD in human-computer interaction, demonstrating a head tracking program he created called WiiDesktopVR. In a video, he demonstrates how to use the program and how it works. The program has a three dimensional sample image of floating targets on different planes coming out of the background. When the person wearing the head tracking unit moves, the image changes in response to this movement, making the image seem like the targets are really there and that the monitor is just a frame into a virtual reality. As the person moves closer to the image, the targets seem to pop out of the screen, out in front of the actual monitor.
Goal 3 (Building head tracking unit)
Supplies:
infrared LED (2), goggles (1), battery holders (2), AA batteries (2), soldering gun, solder
We started by figuring out which end of the LED was positive and which end was negative so we could properly solder the wires of the battery holders to the LED. Since the longer end of the LED is the anode, we soldered it to the red wire of the battery holder, and the shorter end to the black wire. We then taped the battery holders and LEDs onto the goggles, completing the head tracking unit. When the operator wants to activate the infrared emission, batteries are inserted into the battery holders. AA batteries were perfect for the LEDs that we purchased because the two batteries we tested were about 1.5 volts, which was the exact voltage required by the LEDs. This design mimics the Wii sensor bar, but is a simpler wireless head tracking unit.
Since infrared light is not in the visible light spectrum, it cannot be seen by humans, which means it was difficult for us to know whether the LEDs worked or not. The program we tested it out on didn't recognize any infrared light through the sensor of the Wiimote, so we had to figure out if the program wasn't working properly or if the light wasn't being emitted. Since fire emits light in the infrared wavelength, we tested out the sensor using a lighter and indeed we saw a little dot moving around on the screen. We then determined that the first time we tried to build the tracking unit, we had the wiring backwards (longer end soldered to the black wire). We knew the longer end was the anode, but in chemistry the anion is negative, while in physics the anode is positive. This was easily fixed by unsoldering and resoldering the LED the correct way, and the head tracking unit was fully working.
Goal 4 (Wiimote mouse)
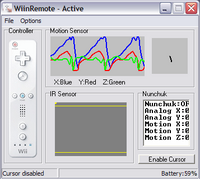
Since we connected the Wiimote to the computer using a USB bluetooth adapter and the location of the Wiimote can be tracked, it is simple to use the remote as a mouse for the computer. This is basically the opposite of head tracking: we mount the LED head tracking unit and use the remote as the mouse input device. We downloaded a program called WiinRemote, which enables the Wiimote to be used as a mouse using either infrared tracking or the accelerometer. The accelerometer can be used for the mouse by tilting the remote forward, backward, left, and right to move the cursor up, down, left, and right, respectively. In the screenshot to the right, you can see the motion sensor tracking graph responding to our shaking of the Wiimote.
This method is not as precise for moving the cursor on the screen compared to infrared tracking, because the infrared detector in the Wiimote is much more sensitive to smaller movements than the accelerometer. The detector in the Wiimote works by tracking the LEDs as two points. As the user moves the remote up, the dots move down. The program running registers this downward movement of the two dots and changes the location of the cursor on the screen, moving it up. This all happens in real time with both the X and Y axis being taken into account.
Goal 5 (Head tracking system)
After the setup of building the head tracking unit and connecting it to the computer through the bluetooth adapter (which was very time consuming and frustrating, because the adapter would not recognize the Wiimote), the WiiDesktopVR program was pretty simple to use. The only variable we needed to put into the configuration file of the program to make it work was the distance in millimeters between the two LEDs on the head tracking unit so that the program would be able to accurately identify the X, Y, and Z axis. The Z axis is necessary for virtual reality so that the user can view the monitor as basically like a frame. As they step closer to the monitor, they can see more of the image, just like as if they were stepping closer to an empty frame. The distance between the LEDs is necessary for the Z axis because as the detector sees the two dots moving farther apart, the program registers this as the Wiimote moving away from the monitor. Likewise, when the dots move closer together, the program recognizes the user moving closer.
The image shows the floating targets that move in response to the wearer of the head tracking unit's movement, as can be seen in the picture. The program worked as planned just like in Lee's video. The weakest link in our setup was the LEDs because the soldering was not perfect so the image intermittently flickered if the battery wasn't seated right or if the head tracking unit was jostled too hard. Also, the fact that we were using a small monitor limited the distance we could travel to the left or right of the screen while still being in the range of the image. To improve our system, we could set up a switch to turn the infrared light on and off without having to insert and remove batteries as well as use a larger screen.
Goal 6 (Javanotes Ch 1)
Up until this point, my only computer programming experience is with Guido van Robot and Python. To familiarize myself with Java, a new and more advanced language for me, I read the introductory chapter of Javanotes (Introduction to Programming Using Java, Fifth Edition) by David Eck at http://math.hws.edu/javanotes/. At the end of the seven sections, I took the chapter quiz.
1. One of the components of a computer is its CPU. What is a CPU and what role does it play in a computer?
- The CPU is the Central Processing Unit and its job is to execute programs. The CPU consists of a square chip with millions of tiny transistors that switch on and off, which can be interpreted as binary digits 1 and 0.
2. Explain what is meant by an "asynchronous event." Give some examples.
- An asynchronous event is a event handled by the CPU that occurs at an unpredictable time. An example of an asynchronous event is when a computer-user clicks a mouse button or keyboard key and the CPU is temporarily interrupted to process the input.
3. What is the difference between a "compiler" and an "interpreter"?
- A compiler takes a high-level computer language program such as Java or C++ and converts it to machine language so that the CPU can execute it. An interpreter acts like a CPU itself and runs in a loop in which it reads the instructions of a program one by one, executing the corresponding machine language commands. Because of the loop process required, compiled programs are faster than interpreted programs.
4. Explain the difference between high-level languages and machine language.
- Machine language is made up of simple instructions that can be executed by the CPU. High-level languages are what almost all programs are written in. In order for the CPU to execute high-level language programs, they must first be translated to machine language. High-level languages are more user-friendly and simpler to develop. Machine language is like bleep bleep bloop.
5. If you have the source code for a Java program, and you want to run that program, you will need both a compiler and an interpreter. What does the Java compiler do, and what does the Java interpreter do?
- The Java compiler converts the program written in Java into Java byte-code, which is the machine language for the Java virtual machine. The virtual machine installed on the computer then interprets the Java byte-code to run the program. Java is a versatile language in this way because a Java program can be run on any computer that has a Java byte-code interpreter installed.
6. What is a subroutine?
- A subroutine is a set of instructions grouped together and given a name that can be substituted for the same set of instructions later on in the program. Subroutines help to save typing and organize programs.
7. Java is an object-oriented programming language. What is an object?
- An object is a module comprised of data and subroutines (states and messages). The states can respond to the messages. For example, if the state is a list of names and the message is telling it to print the data, in response the names will be printed.
8. What is a variable? (There are four different ideas associated with variables in Java. Try to mention all four aspects in your answer.)
- A variable is a memory location assigned a name so that it can be later used in the program. The four types of variables are integers (e.g. -1, 2), floating point numbers (8.16, 15.0), characters ('X', ';'), and strings ("Hello World!", "You need more rams.")
9. Java is a "platform-independent language." What does this mean?
- This means that Java programs can be run on any platform (Windows, Mac, Linux) because Java utilizes a virtual machine interpreter. The interpreter software is different for each platform, but the actual compiled Java program can be run on any computer that has the virtual machine installed.
10. What is the "Internet"? Give some examples of how it is used.
- The Internet is a world-wide network of millions of computers. It can be used for e-mail, instant messaging, file sharing, and accessing the World-Wide Web. Each service th at the Internet provides has its own set of standards, or protocols, that enable it to be interoperable and seamless.
Goal 7 (Install Java)
In order to easily run JDK (Java Development Kit) files through command line in Windows, a PATH variable must be assigned after installing the JDK software.
I installed JDK and jEdit (a programming text editor with syntax highlighting.) JDK is the "Java virtual machine" that converts Java code into Java bytecode. Java bytecode is the machine language for the Java virtual machine. The reason the Java code isn't converted directly to the machine code of my CPU is because Java is made to work on any computer system that has the virtual machine installed, which makes it a versatile high-level programming language.
To set the PATH variable on my Windows computer, I had to edit the "System variables" list (Start > Control Panel > System > Advanced > Environment Variables). Under the "Path" variable, I had to add the JDK directory (C:\Program Files\Java\jdk1.6.0_11\bin) to the list of other Path directories.
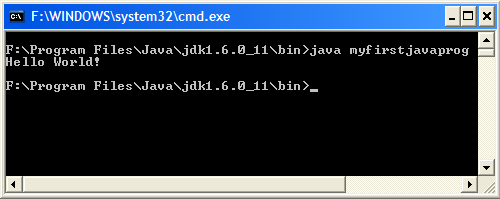
I used the following sample Java code[9] to test out the Path in command line:
class myfirstjavaprog
{
public static void main(String args[])
{
System.out.println("Hello World!");
}
}
I compiled the Java code using the javac command, creating a .class file in the directory. I then executed the program, resulting in the text "Hello World!"
Goal 8 (Javanotes Ch 2.1-2.2)
1. Briefly explain what is meant by the syntax and the semantics of a programming language. Give an example to illustrate the difference between a syntax error and a semantics error.
- The syntax of a language consists of the rules and vocabulary that allow the program to be compiled and executed. Programs that contain syntax errors are rejected and fail to compile. The semantics of a program is its meaning. A program with correct semantics does what you wanted it to do. An example is if your syntax was correct, that is your code was written properly with no mistakes, but the result is "!dlroW olleH" instead of "Hello World!". There is no error in compiling because all of the syntax is correct, but the semantics are wrong because the program did not do what it was meant to do.
2. What does the computer do when it executes a variable declaration statement. Give an example.
See also
References
- ↑ http://www.wisegeek.com/what-is-a-packet-sniffer.htm
- ↑ http://blog.passwordresearch.com/2007/08/how-password-policy-requirements-impact.html
- ↑ http://mathcircle.berkeley.edu/BMC3/rsa/node4.html
- ↑ http://msdn.microsoft.com/en-us/library/aa302352.aspx
- ↑ http://groups.google.com/group/Calls-Chats-and-Voicemail/msg/e49343f783a06a1e
- ↑ http://www.quickonlinetips.com/archives/2008/07/secure-https-gmail/
- ↑ http://docs.sun.com/source/816-6156-10/contents.htm#1046261
- ↑ http://kb.iu.edu/data/anjv.html
- ↑ http://www.javacoffeebreak.com/java101/java101.html