AJ McLennan
Contents
First Quarter
Goals for First Quarter
- Set up a small network
- Install Server OS.
- Set up Mail Server.
- Make Network work, computers working together and commutating.
- Set up firewall.
- Experiment with Network Security.
- Research packet sniffing.
- Install talk, or some other commutation means.
- Find and install a program to sniff packets.
- Successfully intercept a packet.
- Try to reverse a password hash.
- Try to 'hack' into the firewall.
First Quarter Goal Completion
- Setting up our Network
- I installed the server version of Ubuntu on my computer then got an xubuntu GUI to make it easier.
- While my computer has the capiblity of being a mail server, it hasn't been set up yet.
- We have Set up a Small network with three computers. Two running Xubuntu and my computer is running the server edition of ubuntu with an xubuntu GUI.
- We are still waiting on a Network card to set up our fire wall.
- Experimenting with Network Security
- We researched packet sniffing and found a program Wireshark that sniffs packets.
- We all had pidgin install already on our machines. Pidgin is an instant messaging service that can use AIM, MSN messenger or other hosts.
- We found Wireshark in our research and installed it on Willie's and Nick's computers.
- We successfully intercepted many packets. This long list included an e-mail, multiple g-mail chat messages, AIM messages, and a password hash.
- Once we intercepted a password hash we tried our best to reverse it. As of yet we are unable to reverse the hash.
- We have not tried an attack on a firewall yet.
Second Quarter
Goals for Second Quarter
- Research Magnetic strip cards.
- Understand Low coercitivity and High coercitivity.
- Understand The difference between the three tracks and how they are separated.
- Build Magnetic strip reader.
- Connect cat5 wire and db-15 connector
- Modify track reader to read the 3rd track, enabling multi-track reading.
- Find or create software to read and write code on magnetic cards.
- Swipe cards such as credit cards and drivers licenses to see what is stored on them
- Learn to Program Magnetic strips
- Find out if metro cards are Low or High coercitivity.
- Research the code for metro cards.
- Put money on metro cards
Goal Completion for Second Quarter
- I reasearched magnetic stipe cards
- Low coercitivity and High coercitivity is how hard it is to change the information on magnetic stripes
- The three tracks store different information on cards in different forms. For example on a credit card the information is all the same on each track, the difference is how they are stored, hex, binary, or ASCII. The tracks are separated by an unmagnetized portion of the card that on the stripe
- I built a card reader.
Third Quarter
At first we wanted to make the magstripe reader actually work, then see if we couldn't build or modify it to write on the magstripe cards as well. After a bit of tinkering and research we realized that we couldn't build a writer in a quarter much less the rest of the year. So we took a different course and decided to try to attack a WEP encrypted wireless network
Goal Documentation for Third Quarter
- First we set up a wireless router and encryped it with a random WEP key.
- Next we tried to get one of the computers left over from our network to connect to the network with a wireless USB card. But drivers for Ubuntu and the wireless USB card were almost impossible to find, and when they were found the instructions on how to download and install were about as unclear as pond water. So we decided to dual-boot Willie's laptop. Which solved our problem of needing a computer with wireless capabilities
- Once we had our network set up we researched WEP security and programs that would help us crack the key.
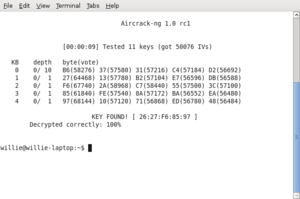
- Willie found a program called Aircrack and then went about installing it on his laptop and configuring his wireless card so it could perform packet injection
- I brought my laptop in and connected to the wireless network while Willie did a client-present attack, which involved him collecting all the packets that my laptop and the router sent to each other.
- After Willie's laptop had collected over 100.000 packets the program tried to find the key and did so successfully.
- After we had cracked the the key we both went our separate ways. I decided to try and create a project using a micro controller. I researched micro controllers and found this website that contained a couple of tutorials about programing a micro controller.
Fourth Quarter
I was talking to a friend of mine about a game we used to play called murder, where one person was the murderer, one person was the detective, and everybody else were victims. When we used to play it we had to play in the dark and stay in one room (so the game wouldn't last all night). As we were talking we decided that we would like to play the game again, expect with a much bigger area, no time limit, and more people. So I thought of a way to replace the little pieces of paper that had "murderer", "detective", and "victim" written on them. I remembered reading somewhere that python could send e-mails, that coupled with the fact that e-mails can be sent to phones as text messages I figured I could write a code to randomly choose two people, one murderer and one detective, then send text messages(e-mails) to those two and send every body else a text message to tell them they're victims.