Willie Stehm 3rd Quarter
From WLCS
Contents
- 1 Main Focus of This Quarter
- 2 Ten Goals for Third Quarter
- 3 Third Quarter Goal Documentation
- 3.1 1) Dual boot Laptop to a Vista Ubuntu 8.10 setup
- 3.2 2) Installing new wireless card
- 3.3 3) Configure Packet Injection for Intel 4965agn Wifi card
- 3.4 4) Research WEP Security
- 3.5 5) Conduct a Client-present WEP Attack
- 3.6 6) Document Attack Findings
- 3.7 7) Research the Anatomy of a Packet
- 3.8 8) Conduct a Clientless WEP Attack
- 3.9 9) Research WPA and WPA2 Wireless Security
- 3.10 10)
Main Focus of This Quarter
- My main focus for this quarter is going to be on wireless security and the methods that exist to exploit said systems.
Ten Goals for Third Quarter
1) Dual boot Laptop to a Vista Ubuntu 8.10 setup [ ]
2) Configure Wireless drivers in Ubuntu [ ]
3) Configure Packet Injection for Intel 4965agn Wifi card [ ]
4) Research WEP Security [ ]
5) Conduct a Client-present WEP Attack [ ]
6) Document Attack Findings [ ]
7) Research the Anatomy of a Packet [ ]
8) Research Clientless WEP Attack [ ]
9) Research WPA and WPA2 Wireless Security [ ]
10) [ ]
Third Quarter Goal Documentation
1) Dual boot Laptop to a Vista Ubuntu 8.10 setup
- After an unsuccessful stint with trying to find linux drivers for an out of date usb wifi dongle AJ and I decided that the fastest way to get our testing off the ground was to dual boot one of our more modern laptops to Ubuntu. I did a bit of research and found that the wireless chipset that my laptop contained (Intel 4965agn) was almost fully supported for what we were trying to carry out so we decided that we would dual boot my laptop. The actual process of dual booting couldn't have been easier. First since my laptop was already running Windows Vista I had to create a hard drive partition that Vista would recognize. The simplest way to do this was to use Vista's built in "Disk Management" suite to help create a partition for Ubuntu. Here is where I ran into my first problem. When I opened up the Disk Management suite Vista told me that I could only make an 8 gig partition, no where near enough for Ubuntu and quite weird since I had almost 100 gigs of free space. I looked up possible reasons for this but none of the solutions I found worked. I defragmented the hard drive, turned on and off multiple vista settings and nothing worked. Finally I found one site that suggested that this was a problem with the Disk Management suite and to use a third party disk partitioner. This is were the real problems started! I found a free GUI partitioner that seemed to work very well. It was well organized, simple to use and everything. I wrote my new partition to disk and was told to reboot to finish the process. I followed the directions and much to my surprise was greeted with the blue screen of death instead of the happy windows welcome screen. I tried everything. Booting into safe mode resulted in a giant fail. Using another bootable disk partitioner to delete the new partition failed, so finally I just resorted to bombing the entire system and installing from my system restore disks. Since I had already backed everything up this wasn't that bad, and the best part of all, after the clean install Vista's Disk Management suite started working and allowed me to make a normal sized partition. I then moved onto the Ubuntu install.
- The Ubuntu install was by far the easiest part of the process. I just popped in my newly burnt Ubuntu 8.10 ISO and followed the onscreen instructions. When it got to the area of where to install I just selected "Guided - use largest free space" and that was it. Booting into my new Ubuntu system I saw that Ubuntu had recognized my wireless card during install and already installed my drivers successfully solving my initial problem of not having a working wireless connection using linux.
2) Installing new wireless card
3) Configure Packet Injection for Intel 4965agn Wifi card
- Packet injection is defined as "a computer networking term which refers to sending a packet on a network into an already established connection, usually by a party not otherwise participating in the said connection. This is accomplished by crafting a packet using raw sockets. Sometimes IP address spoofing is used". When trying to carry out a WEP attack this is used to help speed the process of packet gathering. A packet injection enabled wireless card would send out a fake request to the wireless access point in order to gain a response (in the form of packets) from it. These responses are then added to the pool of collected packets and analyzed later to decrypt the WEP key. Since packet injection isn't used in normal everyday function of wireless cards, the drivers for the card must first be patched to enable it. I did a bit of research and found that packet injection for my wireless card (Intel 4965agn) was widely supported which eased in the process of enabling this vital function.
4) Research WEP Security
- Background
- Short for Wired Equivalent Privacy, WEP was introduced in 1997 to provide users with wireless security that was supposed to be on par with wired security. The basic 64-bit original version of WEP relys on using a 40-bit secret key attached to a 24-bit initialization vector. These two are then XORed together and the combination of the 40-bit secret key and the 24-bit initialization vector creates what is known as the RC4 traffic key. The secret key must be known by the user and the access point that it is associating with in order for the two to work together and successfully send packets back and forth. To send packets back and forth the the packet to be send is first encrypted with the traffic key and sent to its destination. Once received the computer or access point just does the reverse and decrypts the packet back to plain text instructions. While this sounds secure, beginning in 2001 many flaws were found in the system that now allow people to decrypt WEP just by listening in on packet traffic.
- Flaws
- One of the prerequisites of using a stream cipher such as RC4 is that the same initialization vector key never be used twice. While that doesn't seem hard, on a busy network with upwards of a million packets being sent every five to six minutes there is only a limited number of combinations that a 24-bit initialization vector can make. This then requires that the same initialization vector be used over creating a major security flaw. If a person monitors network traffic and collects enough packets, he or she could then compare the packets for similarities, find the shared values between them, and in turn discover the secret key.
5) Conduct a Client-present WEP Attack
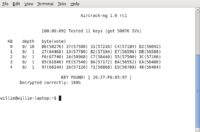
- To start I installed the aircrack-ng suite on the Ubuntu partition on my laptop. The aircrack-ng suite contains a multiple tools all which are specialized for wireless network exploitation. AJ and I decided to start our testing by doing the simplest of attacks. We set up a wireless router with a 64-bit wep key. Next AJ connected to the network and started surfing the web as a normal user would do. In this case AJ acted as a client who was correctly authenticated and associated with our access point. With my laptop I then started up, but did not connect to the wireless network. My first step was to use airmon-ng (one of aircrack-ng's many tools) to put my wireless card into monitor mode. By being in monitor mode my card was able to listen in on all wireless traffic in the surrounding area. Next, I fired up airodump-ng, a program used to show the surrounding networks and clients that are associated to each one. I found our network and at the same time I was able to view the mac address of the access point, the clients already associated to it and their mac address, the wireless channel, the power of the signal, and other useful information. I wrote down the mac address of the access point and also AJ's mac address. Later I started a more specific command on airodump-ng that allowed me to focus only on my desired network collecting packets that were being sent to and from AJ's machine by using the obtained mac addresses. My next step was to start up aireplay-ng (another one of aircrack-ng's tools that utilized the packet injection features of my wireless card) and start injecting packets into the access point. By doing this I was essentially probing the network up to 500 times per second to gain a response. The access points responses were then added to the pool of already collected packets and sped up the entire process. Once the number of packets reached in excess of 250,000 (which took around four to five minutes) I stopped injecting and collecting packets. The final step was to use aircrack-ng to analyze initialization vectors of the collected packets. By doing this aircrack-ng was able to compare packets for similarities which allowed it to discover the secret key and crack the wireless network all in about seven minutes.
6) Document Attack Findings
- From start to finish the entire attack only took around seven minutes. The key was obtained and then tested to confirm its integrity. Everything worked. AJ and I were astonished at how easy it was to crack wep network keys. The very first thing I did was to go home and analyze the networks surrounding my house. Out of ten networks, seven utilized wep security features including my network. I immediately logged into my wireless router settings and changed my security methods from the flawed wep to WPA2 with AES. While WPA2 is not perfect and is still able to be cracked, it far harder to do than the five to seven minute process that AJ and I recreated. On top of that the newer version of WPA2 that I implemented included added AES algorithm features that encrypted each sent packet with security that is comparable with what the US government uses to secure top secret documents.
7) Research the Anatomy of a Packet
- When clients and access points wish to communicate they send "packets" of information back and forth to one another. With the rise of the internet and computing in general this process of sending packets back and forth was standardized for ease of use. Today we use the 802.11 standard. A standard 802.11 packet can be seen here. Besides the standard 802.11 packet, the 802.11 standard utilizes different frames that are placed in a packet to give it a specific purpose. Below is a list of the frames that will be used through out AJ and Is testing (Please note that this is not a complete list of all 802.11 frames but only a list of the frames that we encountered).
- Authentication frames
- Frames that are used to allow the access point to either accept or reject a client due to the identity of their network interface card (usually defined by the users MAC address).
- De-authentication frames
- Essentially the opposite of the authentication frame by ceasing a connection with a given client.
- Association request frame
- Frame containing information about the client so that the access point can synchronize and work with it.
- Association response frame
- Notifies the client of either an acceptance or rejection of their given information.
- Reassociation request frame
- If a client disconnects from an access point or the connection is dropped for a variety of reasons, the client will send a reassociation request frame in order to restore the connection with the access point.
- Reassociation response frame
- Same as the association response frame and either sends an acceptance or rejection notice to the client.
- Along with the 802.11 protocol we also relied heavily on ARP requests and replies during the clientless attack section. These ARP requests and replies lie under the TCP/IP protocol. These ARP packets (ARP standing for Address Resolution Protocol) help to resolve a IP address into a physical hardware address such as a MAC address.
8) Conduct a Clientless WEP Attack
- Clientless attacks essentially work in the same way as a client present attack except with a few differences. Since there is no client already authenticated and associated we are unable to fake their mac address and collect the packets that would normally be sent to them. To counter this we must conduct a fake authentication and association before we are able to precede. If this is not done then the access point will not recognize the attacking computer and essentially refuse to "talk" to them resulting in an inability to collect packets. To solve this problem we must do a few things. First we have to check and see if MAC filtering is enabled. MAC filtering is an added security feature that some access points utilize that allows the owner to set a select list of of MAC addresses that can gain access to the network. When a client is trying go connect to the network the access point cross references their MAC address to the list that it has to see if they are allowed to connect. If their MAC address is present on the list the client is then allowed to precede with the authentication and association process. If they are not present on the list the access point refuses communication with that client. If MAC filtering is not enabled we are able to just authenticate and associate ourselves with the access point and then start collecting packets like normal.
- While this might seem fool proof, by utilizing ARP requests and replies one is able to by pass the access points mac filtering in a few steps. First by using the aireplay-ng tool of the aircrack-ng suite the user sends out a packet that contains de-authentication frames to the access point. This packet causes the access point to "de-authenticate" every client that would be associated to the access point. As a result of this the access point starts to send out ARP requests in an effort to re-authenticate clients. In a normal senario ARP requests work like this. An access point or computer sends out an ARP request that essentially asks "Who has this IP address". A computer or access point then sends out an ARP reply that says "I have that IP address and my MAC address is [blank]". This request and reply are sent out to the entire network, except only the computer that actually has that IP address recognizes and responds to the request. It is this request and reply process that allows us to utilize ARP replies in clientless attacks. After we de-authenticate all would be clients the access point starts to send out ARP requests like stated before. At this time we start up the airodump-ng tool to start collecting packets. Next our attacking computer than waits to intercept one of the ARP request that the access point has sent out. Once received our computer starts replaying the ARP reply, meaning that it retransmits the given ARP request back to the access point. This in turn causes the access point to send out a new ARP request that contains a new initialization vector. Each time this cyclic process occurs the computer collects the new initialization vectors. After enough iv's are collected we are able to decrypt the secret key just like if we were doing a client present attack.
9) Research WPA and WPA2 Wireless Security
- With the obvious flaws in the WEP system, starting in 1999 a new system, WPA, became available to users. Later in 2004 WPA was again preceded by WPA2 which offers even greater security.
- How WPA works
- WPA works similar to WEP but with a few key differences that account for its greater security. Looking back on the way WEP worked we remember that the 40-bit secret key is just XORed with the 24-bit initialization vector. This simple process is what allowed people to listen in on networks and then easily reverse the process to gain access to the secret key. While WPA does employ the same RC4 cipher stream to create the IV section it is no longer just XORed with the secret key. WPA utilizes a new system know as TKIP or Temporal Key Integrity Output which securely mixes the secret key and the IV, effectively making it harder for a person to listen in on IVs and then obtain the secret key. This process of mixing the IV with the secret key has now come to be known as dynamic key generation
- How WPA2 works
- Just like how the changes from WEP to WPA were small, the changes from WPA to WPA2 were equally as small but increased security ten fold. In stead of using the old and outdated RC4 cipher stream to create the traffic key, WPA2 uses the new AES or Advanced Encryption Standard as its cipher block making it much safer for the transfer of sensitive data.